Web Services Security specification - a chronology
The development of the Web Services Security specification includes information on the Organization for the Advancement of Structured Information Standards (OASIS) Web Services Security specification. The OASIS Web Services Security specification serves as a basis for securing web services in WebSphere Application Server.
IBM WAS supports JAX-WS and JAX-RPC. a standards-based annotations model. Although JAX-RPC and applications are still supported, take advantage of the easy-to-implement JAX-WS programming model to develop new web services applications and clients.best-practices
Advantages of using JAX-WS in WAS include:
- The configuration of qualities of service (QoS) is simplified when using policy sets. Policy sets combine configuration settings, including those for transport and message-level configuration. Policy sets and general bindings can be reused across multiple applications, making web services QoS more consumable.
- WS-Security for JAX-WS is supported in both a managed environment, such as a Java EE container, and unmanaged environments, such as Java Platform, Standard Edition (Java SE 6). In addition, there is an API for enabling WS-Security in the JAX-WS client.
Non-OASIS activities
Web services is gaining rapid acceptance as a viable technology for interoperability and integration. However, securing web services is one of the paramount quality of services that makes the adoption of web services a viable industry and commercial solution for businesses. IBM and Microsoft jointly published a security white paper on web services entitled Security in a Web Services World: A Proposed Architecture and Roadmap. The white paper discusses the following initial and subsequent specifications in the proposed Web Services Security roadmap:
- Web service security
- This specification defines how to attach a digital signature, use encryption, and use security tokens in SOAP messages.
- WS-Policy
- This specification defines the language used to describe security constraints and the policy of intermediaries or endpoints.
- WS-Trust
- This specification defines a framework for trust models to establish trust between web services.
- WS-Privacy
- This specification defines a model of how to express a privacy policy for a web service and a requester.
- WS-SecureConversation
- This specification defines how to exchange and establish a secured context, which derives session keys between web services.
- WS-Authorization
-
This specification defines the authorization policy for a Web service. However, the WS-Authorization specification has not been published. The existing implementation of Web Services Security is based upon the Web Services for Java EE or Java Specification Requirements (JSR) 109 specification. The implementation of Web Services Security leverages the Java EE role-based authorization checks. For conceptual information, read about role-based authorization. If we develop a web service that requires method-level authorization checks, then we must use stateless session beans to implement the web service. See securing enterprise bean applications.
If we develop a web service implemented as a servlet, we can use coarse-grained or URL-based authorization in the web container. However, in this situation, we cannot use the identity from Web Services Security for authorization checks. Instead, we can use the identity from the transport. If we use SOAP over HTTP, then the identity is in the HTTP transport.
This following figure shows the relationship between these specifications:
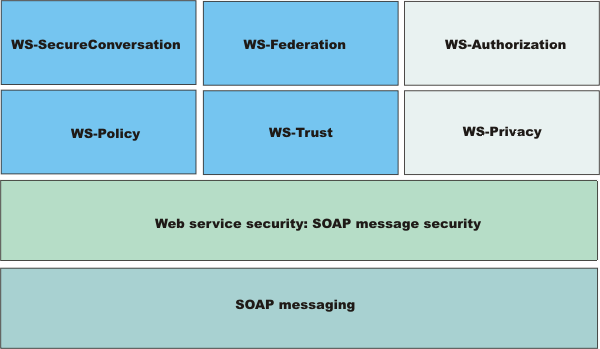
In April 2002, IBM, Microsoft, and VeriSign proposed the Web Services Security (WS-Security) specification on their websites as depicted by the green box in the previous figure. This specification included the basic ideas of a security token, XML digital signature, and XML encryption. The specification also defined the format for user name tokens and encoded binary security tokens. After some discussion and an interoperability test based on the specification, the following issues were noted:
- The specification requires that the Web Services Security processors understand the schema correctly so that the processor distinguishes between the ID attribute for XML digital signature and XML encryption.
- The freshness of the message, which indicates whether the message complies with predefined time constraints, cannot be determined.
- Digested password strings do not strengthen security.
In August 2002, IBM, Microsoft, and VeriSign published the Web Services Security Addendum, which attempted to address the previously listed issues. The following solutions were addressed in the addendum:
- Require a global ID attribute for XML signature and XML encryption.
- Use time stamp header elements that indicate the time of the creation, receipt, or expiration of the message.
- Use password strings that are digested with a time stamp and nonce, which is a randomly generated token.
The specifications for the blue boxes in the previous figure have been proposed by various industry vendors and various interoperability events have been organized by the vendors to verify and refine the proposed specifications.
OASIS activities
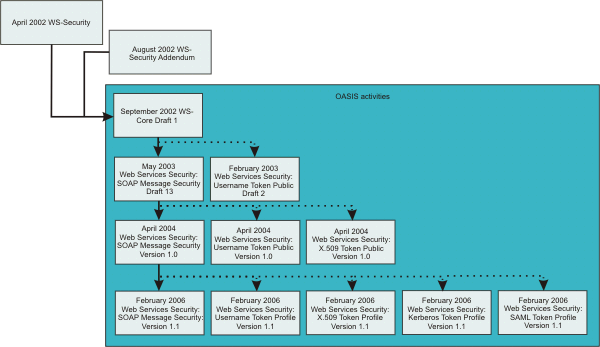
In June 2002, OASIS received a proposed Web Services Security specification from IBM, Microsoft, and VeriSign. The Web Services Security Technical Committee (WSS TC) was organized at OASIS soon after the submission. The technical committee included many companies including IBM, Microsoft, VeriSign, Sun icrosystems, and BEA Systems.
In September 2002, WSS TC published its first specification, Web Services Security Core Specification, Working Draft 01. This specification included the contents of both the original Web Services Security specification and its addendum.
The coverage of the technical committee became larger as the discussion proceeded. Because the Web Services Security Core Specification allows arbitrary types of security tokens, proposals were published as profiles. The profiles described the method for embedding tokens, including Security Assertion Markup Language (SAML) tokens and Kerberos tokens embedded into the Web Services Security messages. Subsequently, the definitions of the usage for user name tokens and X.509 binary security tokens, which were defined in the original Web Services Security Specification, were divided into the profiles.
WAS Versions 5.0.2, 5.1, and 5.1.1 support the following specifications:
- Web Services Security: SOAP Message Security Draft 13 (formerly Web Services Security Core Specification)
- Web Services Security: Username Token Profile Draft 2
In April 2004, the Web Service Security specification (officially called Web Services Security: SOAP Message Security Version 1.0) became the Version 1.0 OASIS standard. Also, the Username token and X.509 token profiles are Version 1.0 specifications. WAS 6 and later support the following Web Services Security specifications from OASIS:
- Web Services Security: SOAP Message Security 1.0 specification
- Web Services Security: Username Token 1.0 Profile
- Web Services Security: X.509 Token 1.0 Profile
In February 2006, the core Web Service Security specification was updated and became the Version 1.1 OASIS standard. Also, the Username token, X.509 token profile, and Kerberos token profile were updated to the Version 1.1 specifications. Portions of the following Web Services Security specifications from OASIS are supported in WAS, specifically signature confirmation, encrypted header, and thumbprint references:
- OASIS: Web Services Security: SOAP Message Security 1.1 (WS-Security 2004) OASIS Standard Specification, 1 February 2006
- OASIS: Web Services Security UsernameToken Profile 1.1 OASIS Standard Specification, 1 February 2006
- OASIS: Web Services Security X.509 Certificate Token Profile 1.1 OASIS Standard Specification, 1 February 2006
The following specification describes the use of Kerberos tokens with respect to the Web Services Security message security specifications. The specification defines how to use a Kerberos token to support authentication and message protection: OASIS: Web Services Security Kerberos Token Profile 1.1 OASIS Standard Specification, 1 February 2006.
In 2007, the OASIS Web Services Secure Exchange Technical Committee (WS-SX) produced and approved the following specifications. Portions of these specifications are supported by WAS v7 and later.
The following figure shows the various Web Services Security-related specifications.
WAS also provides plug-in capability to enable security providers to extend the runtime capability and implement some of the higher level specifications in the Web Service Security stack. The plug-in points are exposed as Service Provider Programming Interfaces (SPI). For more information on these SPIs, see Default implementations of the Web Services Security service provider programming interfaces.
Web Services Security specification 1.0 development
The OASIS Web Services Security specification is based upon the following World Wide Web Consortium (W3C) specifications. Most of the W3C specifications are in the standard body recommended status.
- XML-Signature
Syntax and Processing
W3C recommendation, February 2002 (Also, IETF RFC 3275, March 2002)
- Canonical XML Version 1.0
W3C recommendation, March 2001
- Exclusive XML
Canonicalization Version 1.0
W3C recommendation, July 2002
- XML-Signature
XPath Filter v2.0
W3C Recommendation, November 2002
- XML Encryption
Syntax and Processing
W3C Recommendation, December 2002
- Decryption
Transform for XML Signature
W3C Recommendation, December 2002
These specifications are supported in WAS in the context of Web Services Security. For example, we can sign a SOAP message by specifying the integrity option in the deployment descriptors. There is a client side API an application can use to enable Web Services Security for securing a SOAP message.
The OASIS Web Services Security Version 1.0 specification defines the enhancements used to provide message integrity and confidentiality. It also provides a general framework for associating the security tokens with a SOAP message. The specification is designed to be extensible to support multiple security token formats. The particular security token usage is addressed with the security token profile.
Specification and profile support in WAS
OASIS is working on various profiles. See Organization for the Advancement of Structured Information Standards Committees.
The following list includes of the published draft profiles and OASIS Web Services Security technical committee work in progress.
WAS does not support these profiles:
- Web Services Security: SAML token profile 1.0
- Web Services Security: Rights Expression Language (REL) token profile 1.0
- Web Services Security: SOAP Messages with Attachments (SwA) profile 1.0
Support for Web Services Security draft 13 and Username token profile draft 2 is deprecated in WAS 5.0.2, 5.1.0 and 5.1.1. For migration information, see Migrate Web Services Security-enabled JAX-RPC applications from Java EE Version 1.3 to Version 1.4.
The wire format of the SOAP message with Web Services Security in Web Services Security Version 1.0 has changed and is not compatible with previous drafts of the OASIS Web Services Security specification. Interoperability between OASIS Web Services Security Version 1.0 and previous Web Services Security drafts is not supported. However, it is possible to run an application based on Web Services Security draft 13 on WAS v6 and later. The application can interoperate with an application based on Web Services Security draft 13 on WAS v5.0.2, 5.1 or 5.1.1.
WAS supports both the OASIS Web Services Security draft 13 and the OASIS Web Services Security 1.0 specification. But in WAS v6 and later, the support of OASIS Web Services Security draft 13 is deprecated. However, applications that were developed using OASIS Web Services Security draft 13 on WAS 5.0.2, 5.1.0 and 5.1.1 can run on WAS v6 and later. OASIS Web Services Security Version 1.0 support is available only for Java EE Version 1.4 and later applications. The configuration format for the deployment descriptor and the binding is different from previous versions of WAS. We must migrate the existing applications to Java EE 1.4 and migrate the Web Services Security configuration to the WAS v6 format.
Other Web Services Security specifications development
The most recently updated versions of the following OASIS Web Services Security specifications are supported in WAS in the context of Web Services Security:
- WS-Trust Version 1.3
The Web Services Trust Language (WS-Trust) uses the secure messaging mechanisms of Web Services Security to define additional primitives and extensions for the issuance, exchange and validation of security tokens. WS-Trust enables the issuance and dissemination of credentials within different trust domains. This specification defines ways to establish, assess the presence of, and broker trust relationships.
- WS-SecureConversation Version 1.3
The Web Services Secure Conversation Language (WS-SecureConversation) is built on the WS-Security and WS-Policy models to provide secure communication between services. WS-Security focuses on the message authentication model but not a security context, and thus is subject several forms of security attacks. This specification defines mechanisms for establishing and sharing security contexts, and deriving keys from security contexts, to enable a secure conversation. By using the SOAP extensibility model, modular SOAP-based specifications are designed to be composed with each other to provide a rich messaging environment.
- WS-SecurityPolicy Version 1.2
Web Services Security Policy (WS-Policy) provides a general purpose model and syntax to describe and communicate the policies of a web service. WS-Policy assertions express the capabilities and constraints of a particular web service. WS-PolicyAttachments defines several methods for associating the WS-Policy expressions with web services (such as WSDL). The Web Services Security specifications have been updated following the re-publication of WS-Security Policy in July 2005, to reflect the constraints and capabilities of web services that are using WS-Security, WSTrust and WS-SecureConversation. WS-ReliableMessaging Policy has also been re-published in 2005 to express the capabilities and constraints of web services implementing WS-ReliableMessaging.
Web Services Interoperability Organization (WS-I) activities
Web Services Interoperability Organization (WS-I) is an open industry effort to promote web services interoperability across vendors, platforms, programming languages and applications. The organization is a consortium of companies across many industries including IBM, Microsoft, Oracle, Sun, Novell, VeriSign, and Daimler Chrysler. WS-I has developed Basic Security Profile (BSP) 1.0 and 1.1 versions. Both BSP 1.0 and 1.1 versions consist of a set of non-proprietary web services specifications that clarifies and amplifies those specifications to promote Web Services Security interoperability across different vendor implementations.
WAS JAX-WS WS-Security supports the following specifications:
- Basic Profile Version 1.2 (BP 1.2): http://ws-i.org/profiles/basicprofile-1.2-2010-11-09.html
- Basic Profile v2.0 (BP 2.0): http://ws-i.org/profiles/basicprofile-2.0-2010-11-09.html
- Basic Security Profile Version 1.0 (BSP 1.0): http://www.ws-i.org/profiles/basicsecurityprofile-1.0.html
- Basic Security Profile Version 1.1 (BSP 1.1): http://www.ws-i.org/profiles/basicsecurityprofile-1.1.html
- Reliable Secure Profile 1.0 (RSP 1.0): http://www.ws-i.org/profiles/ReliableSecureProfile-1.0-2010-11-09.html
Related: