WAS v8.5 > Secure applications > Secure web services > Secure web services > Web Services Security concepts > Web Services Security concepts > Web Services Security provides message integrity, confidentiality, and authentication > High-level architecture for Web Services Security
Overview of platform configuration and bindings
The Web Services Security policy is specified in the IBM extension of the web services deployment descriptors when using the JAX-RPC programming model, and in policy sets when using the JAX-WS programming model. Binding information to support the Web Services Security policy is stored in the IBM extension of the web services deployment descriptors for both the JAX-RPC and JAX-WS programming models.
Best practice: IBM WebSphere Application Server supports the JAX-WS programming model and the (JAX-RPC) programming model. JAX-WS is the next generation web services programming model extending the foundation provided by the JAX-RPC programming model. Using the strategic JAX-WS programming model, development of web services and clients is simplified through support of a standards-based annotations model. Although the JAX-RPC programming model and applications are still supported, take advantage of the easy-to-implement JAX-WS programming model to develop new web services applications and clients. best-practices
Due to the complexity of these files, it is not recommended that you edit the deployment descriptor and binding files manually with a text editor because they might cause errors. It is recommended, however, that we use the tools provided by IBM to configure the Web Services Security constraints for an application. These tools are the WAS dmgr console, or an assembly tool. For more information about IBM assembly tools, see the assembly tools information.
We can use the policy set function of the WAS to simplify the web services configuration because policy sets group security and other web services settings into reusable units. Policy sets are assertions about how quality of services is defined. A policy set incorporates policy types, and their settings.
In addition to the application deployment descriptor and binding files, WAS Versions 6 and later have a server level Web Security Services configuration. These configurations are global for all applications. Because WAS v6 and later support 5.x applications, some of the configurations are valid for v5.x applications only and some are valid for v6 and later applications only.
The following figure represents the relationship of the application deployment descriptor and binding files to the cell (WAS, Network Deployment only) or server level configuration.

Platform configuration
The following options are available in the dmgr console:
- Nonce cache timeout
- This option, which is found on the cell level (WAS, Network Deployment only) and server level, specifies the cache timeout value for a nonce in seconds.
- Nonce maximum age
- This option, which is found on the cell level (WAS, Network Deployment only) and server level, specifies the default life span for the nonce in seconds.
- Nonce clock skew
- This option, which is found on the cell level (WAS, Network Deployment only) and server level, specifies the default clock skew to account for network delay, processing delay, and so on. It is used to calculate when the nonce expires. Its unit of measurement is seconds.
- Distribute nonce caching
- This feature enables you to distribute the cache for the nonce to different servers in a cluster. It is available for WAS v6.0.x and later.
The following features can be referenced in the application binding:
- Key locator
- This feature specifies how the keys are retrieved for signing, encryption, and decryption. The implementation classes for the key locator are different in WAS Versions 6 and later and v5.x.
- Collection certificate store
- This feature specifies the certificate store for certificate path validation. It is typically used for validating X.509 tokens during signature verification or constructing the X.509 token with a certificate revocation list that is encoded in the PKCS#7 format. The certificate revocation list is supported for WAS v6.x and later applications only.
- Trust anchors
- This feature specifies the trust level for the signer certificate and is typically used in the X.509 token validation during signature verification.
- Trusted ID evaluators
- This feature specifies how to verify the trust level for the identity. The feature is used with identity assertion.
- Login mappings
- This feature specifies the login configuration binding to the authentication methods. This feature is used by WAS v5.x applications only and it is deprecated.
Default bindings
The configuration of the default cell level and default server level bindings has changed in WAS. Previously, you could configure only one set of default bindings for the cell, and optionally configure one set of default bindings for each server. In version 7.0 and later, we can configure one or more general provider bindings and one or more general client bindings. However, only one general provider binding and one general client binding can be designated as the default.
The following figure shows the relationship between the application EAR file and the ws-security.xml file.

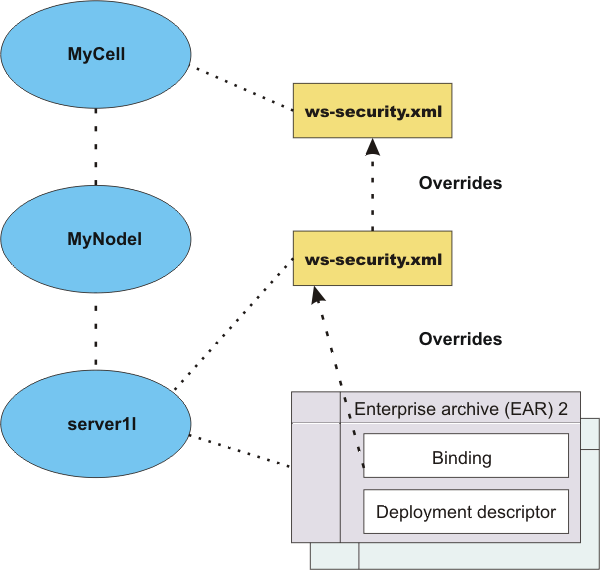
Applications EAR 1 and EAR 2 have specific bindings in the application binding file. However, applications EAR 3 and EAR 4 do not have a binding in the application binding file; it must be referenced to use the default bindings defined in the ws-security.xml file. The configuration is resolved by nearest configuration in the hierarchy. For example, there might be key locators named mykeylocator defined in the application binding file and the server level.
If mykeylocator is referenced in the application binding, then the key locator defined in the application binding is used. The visibility scope of the data depends upon where the data is defined. If the data is defined in the application binding, then its visibility is scoped to that particular application. If the data is defined on the server level, then the visibility scope is all of the applications deployed on that server. In general, if data is not meant to be shared by other applications, define the configuration in the application binding level.
The following figure shows the relationship of the bindings on the application, server, and cell (WAS, Network Deployment only) levels.
General bindings
General bindings are used as the default bindings at the cell level or server level. The general bindings that are shipped with WAS are initially set as the default bindings, but we can choose a different binding as the default, or change the level of binding that should be used as the default, for example, from cell level binding to server level binding.
In version 7.0 and later, there are two types of bindings: application specific bindings, and general bindings. Both types of bindings are supported for WS-Security policy sets. General bindings can be shared across multiple applications and for trust service attachments. There are two types of general bindings: one for service providers and one for service clients. Multiple general bindings can be defined for the provider and also for the client.
Subtopics
- Keys
Use keys for XML digital signature and encryption. - Key locator
A key locator is an abstraction of the mechanism that retrieves the key for digital signature and encryption. The Java Authentication and Authorization Service (JAAS) Login Module implementation is used to create the security token on the generator side and to validate (authenticate) the security token on the consumer side. - Trust anchor
A trust anchor specifies the key stores containing trusted root certificates. These certificates are used to validate the X.509 certificate that is embedded in the SOAP message. - Trusted ID evaluator
A trusted ID evaluator is the mechanism that evaluates whether a given ID name is trusted. - Hardware cryptographic device support for Web Services Security
In IBM WAS v6.1 or later, Web Services Security supports the use of cryptographic hardware devices. There are two ways in which to use hardware cryptographic devices with Web Services Security.
Related concepts:
Web services policy sets
Nonce, a randomly generated token
Basic Security Profile compliance tips
Collection certificate store
Development and assembly tools
Related
Manage policy sets
Distributing nonce caching to servers in a cluster
Reference:
Application policy sets page