Single sign-on for HTTP requests using SPNEGO
WAS provides a trust association interceptor (TAI) that uses the Simple and Protected GSS-API Negotiation Mechanism (SPNEGO) to securely negotiate and authenticate HTTP requests for secured resources in WAS.
SPNEGO is a standard specification defined in The Simple and Protected GSS-API Negotiation Mechanism (IETF RFC 2478).
When administrative security is enabled, the SPNEGO TAI is initialized. While processing inbound HTTP requests, the Web authenticator component interacts with the SPNEGO TAI, which is defined and enabled in the security configuration repository. One interceptor is selected and is responsible for authenticating access to the secured resource that is identified in the HTTP request.
The use of TAIs is an optional feature. If no TAI is selected, the authentication process continues normally.
HTTP users log in and authenticate only once at their desktop and are subsequently authenticated (internally) with WAS. The SPNEGO TAI is invisible to the end-user of WebSphere applications. The SPNEGO TAI is only visible to the Web administrator who is responsible for ensuring a proper configuration, capacity, and maintenance of the Web environment.
In addition to WAS security runtime services, some external components are required to completely enable operation of the SPNEGO TAI.
-
![[Windows]](../../windows.gif) Microsoft's Windows 2000 or Windows 2003 Servers with
Active Directory domain and associated Kerberos Key Distribution Center (KDC).
Microsoft's Windows 2000 or Windows 2003 Servers with
Active Directory domain and associated Kerberos Key Distribution Center (KDC).
- A client application, for example, a browser or .NET client, that supports the SPNEGO authentication mechanism, as defined in IETF RFC 2478. Microsoft Internet Explorer V5.5 or later and Mozilla Firefox V1.0 are browser examples.
The authentication of HTTP requests is triggered by the requestor (the client-side), which generates a SPNEGO token. WAS receives this token and validates trust between the requester and WebSphere Application Server. Specifically, the SPNEGO TAI decodes and retrieves the requester's identity from the SPNEGO token. The identity is used to establish a secure context between the requester and the appserver.
The SPNEGO TAI is a server-side solution in WAS. Client-side applications are responsible for generating the SPNEGO token for use by the SPNEGO TAI. The requester's identity in WAS security registry must be identical to that identity the SPNEGO TAI retrieves. An identical match does occur when Microsoft Windows Active Directory server is the LDAP server used in WAS.
A custom login module is available as a plug-in to support custom mapping of the identity from the Active Directory to the WebSphere Application Server security registry.
WAS validates the identity against its security registry and, if the validation is successful, produces a security token and places and returns a cookie to the requester in the HTTP response. Subsequent HTTP requests from this same requester to access additional secured resources in WAS use the LTPA security token previously created, to avoid repeated login challenges.
The challenge-response handshake process is illustrated in the following graphic:
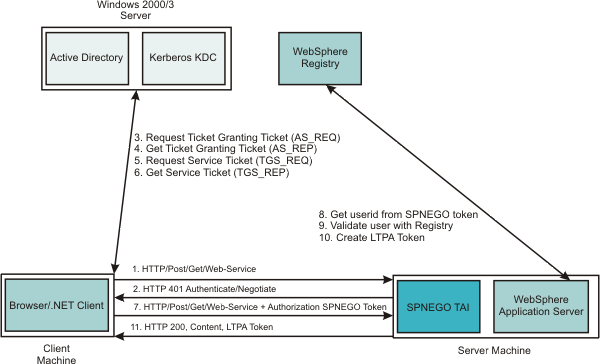
The SPNEGO TAI can be enabled for all or for selected WebSphere Application Servers in a WAS cell configuration. The behavior of each SPNEGO TAI instance is controlled by custom configuration properties that are used to identify, for example, the criteria used to filter HTTP requests, such as the host name and security realm name used to construct the Kerberos Service Principal Name (SPN).
- Setting up the Kerberos configuration properties.
- Setting or adjusting the SPNEGO TAI custom attributes.
- Adjusting the SPNEGO TAI filter settings.
- Use the custom login module to map the identity from the Active Directory to the WAS registry.
- Setting the major and additional JVM attributes.
The Web administrator has access to the following SPNEGO TAI security components and associated configuration data, as illustrated in the following graphic.
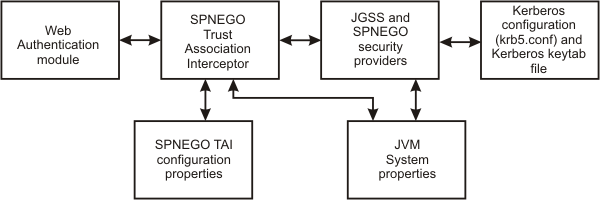
- The Web authentication module and the LTPA mechanism provide the plug-in runtime framework for trust association interceptors.
- The Java Generic Security Service (JGSS) provider is included in the Java SDK...
-
jre/lib/ibmjgssprovider.jar
...and used to obtain the Kerberos security context and credentials that are used for authentication.
IBM JGSS 1.0 is a Java Generic Security Service API (GSSAPI) framework with Kerberos V5 as the underlying default security mechanism. GSSAPI is a standardized abstract interface under which can be plugged different security mechanisms based on private-key, public-key and other security technologies. GSSAPI shields secure applications from the complexities and peculiarities of the different underlying security mechanisms. GSSAPI provides...
- identity and message origin authentication
- message integrity
- message confidentiality
- The Kerberos configuration properties (krb5.conf or krb5.ini ) and Kerberos encryption keys (stored in a Kerberos keytab file) are used to establish secure mutual authentication.
The Kerberos key table manager (Ktab), which is part of JGSS, allows you to manage the principal names and service keys stored in a local Kerberos keytab file. Principal name and key pairs listed in the Kerberos keytab file allow services running on a host to authenticate themselves to the KDC. Before a server can use Kerberos, a Kerberos keytab file must be initialized on the host that runs the server.
Kerberos configuration requirements for SPNEGO TAI highlights the Kerberos configuration requirements for the SPNEGO TAI as well as the use of Ktab.
- The SPNEGO provider supplies the implementation of the SPNEGO authentication mechanism, located at...
-
/$WAS_HOME/java/jre/lib/ext/ibmspnego.jar
- The custom configuration properties control the runtime behavior of the SPNEGO TAI. Configuration operations are performed with the administrative console or scripting facilities.
- JVM system properties control diagnostic trace information for problem determination of the JGSS security provider and use of the property reload feature.SPNEGO TAI JVM configuration attributes describes these JVM configuration attributes
The benefits of having WAS use the SPNEGO TAI include:
-
![[Windows]](../../windows.gif) An integrated single signon environment with Microsoft Windows 2000 or 2003 Servers using Active Directory domain is established.
An integrated single signon environment with Microsoft Windows 2000 or 2003 Servers using Active Directory domain is established.
- The cost of administering a large number of ids and passwords is reduced.
- A secure and mutually authenticated transmission of security credentials from the Web browser or .NET clients is established.
- Interoperability with Web services and .NET applications that use SPNEGO authentication at the transport level is achieved.
Using the SPNEGO TAI in your WAS environment requires planning then implementation.
Implementing the use of the SPNEGO TAI is divided into the following areas of responsibility:
- End user
- The end user must configure the Web browser or .NET application to issue HTTP requests that are processed by the SPNEGO TAI.
- Web administrator
- The Web administrator is responsible for configuring the SPNEGO TAI of WAS to respond to HTTP requests of the client.
- WAS administrator
- The WAS administrator is responsible for configuring WAS and the SPNEGO TAI for optimum installation performance.
Sub-topics
SPNEGO TAI configuration requirements
Related concepts
Single sign-onConfigure WAS environment to use SPNEGO
Configure single sign-on capability with SPNEGO TAI
Creating the Kerberos keytab file
Filtering HTTP requests for SPNEGO TAI
Mapping user Ids from client to server for SPNEGO
Kerberos configuration requirements for SPNEGO TAI
Configure the Kerberos configuration properties
SPNEGO TAI JVM configuration attributes
SPNEGO TAI custom configuration attributes
The Simple and Protected GSS-API Negotiation Mechanism (IEFT RFC 2478)
Single Sign-on Using Kerberos in Java
Kerberos: The Network Authentication Protocol