Add an external repository in a federated repository configuration
Follow this task to add an external repository into a federated repository configuration.
Procedure
- If the LDAP repository to add to your federated repository configuration is previously configured, select the corresponding Repository on the Repository reference panel. To access the Repository reference panel, complete the following steps:
- Click...
Security | Secure administration, applications, and infrastructure | User account repository | Federated repositories | Configure | Add base entry to realm
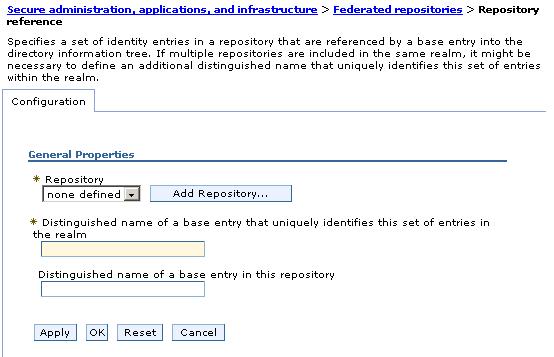
- Click...
- Enter a distinguished name for the realm base entry in the Distinguished name that uniquely identifies... field. This base entry must uniquely identify the external repository in the realm. If multiple repositories are included in the realm, use this field to define an additional distinguished name (DN) that uniquely identifies this set of entries within the realm. For example, repositories LDAP1 and LDAP2 might both use o=ibm,c=us as the base entry in the repository. Use the DN in this field to uniquely identify this set of entries in the realm. For example: o=ibm,c=us for LDAP1 and o=ibm2,c=us for LDAP2. The specified DN in this field maps to the LDAP DN of the base entry within the repository.
- Enter the LDAP DN of the base entry within the repository in the
Distinguished name of a base entry... field. The base entry indicates the starting point for searches in this LDAP directory server. This entry and its descendents are mapped to the subtree that is identified by this unique base name entry field. For example, for a user with a DN of cn=John Doe, ou=Rochester, o=IBM, c=US, specify the LDAP base entry as any of the following options:
ou=Rochester, o=IBM, c=us or o=IBM, c=us or c=us
In most cases, this LDAP DN is the same as the distinguished name for the realm base entry.
If this field is left blank, then the subtree defaults to the root of the LDAP repository. Consult your LDAP administrator to determine if your LDAP repository provides support to search from the root, or create users and groups under the root without defining a suffix beforehand.
In WAS, the distinguished name is normalized according to the LDAP specification. Normalization consists of removing spaces in the base distinguished name before or after commas and equal symbols. An example of a non-normalized base distinguished name is o = ibm, c = us or o=ibm, c=us. An example of a normalized base distinguished name is o=ibm,c=us.
- If the LDAP repository to add to your realm is not previously configured...
- Click Add Repository on the Repository reference panel to configure the LDAP repository. See step 1 to access the Repository reference panel.
- Configure LDAP on the LDAP configuration panel, as described in Configure LDAP in a federated repository configuration.
- Select the new Repository on the Repository reference panel.
- Click Add Repository on the Repository reference panel to configure the LDAP repository. See step 1 to access the Repository reference panel.
- Click OK.
Results
You have added a new or previously configured external repository into your federated repository configuration.
What to do next
- Before you can manage this account with Users and Groups, configure supported
entity types as described in Configure supported entity types in a federated repository configuration.
- After configuring the federated repositories, click Security > Secure administration, applications, and infrastructure to return to the Secure administration, applications, and infrastructure panel. Verify that Federated repositories is identified in the Current realm definition field. If Federated repositories is not identified, select Federated repositories from the Available realm definitions field and click Set as current.
To verify the federated repositories configuration, click Apply on the Secure administration, applications, and infrastructure panel. If Federated repositories is not identified in the Current realm definition field, your federated repositories configuration is not used by WebSphere Application
Server.
- If you are enabling security, complete the remaining steps as specified in Enabling security for the realm. As the final step, validate this setup by clicking Apply in the Secure administration, applications, and infrastructure panel.
- Save, stop, and restart all the product servers (deployment managers, nodes and Application Servers) for changes in this panel to take effect. If the server comes up without any problems, the setup is correct.