Digital signatures
A digital signature is formed by encrypting a representation of a message. The encryption uses the private key of the signatory and, for efficiency, usually operates on a message digest rather than the message itself. See Message digests for more information.
Digital signatures vary with the data being signed, unlike handwritten signatures, which do not depend on the content of the document being signed. If two different messages are signed digitally by the same entity, the two signatures differ, but both signatures can be verified with the same public key, that is, the public key of the entity that signed the messages.
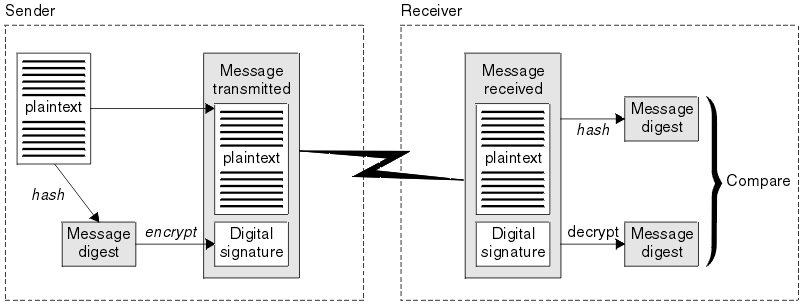
The steps of the digital signature process are as follows:
- The sender computes a message digest and then encrypts the digest using the sender's private key, forming the digital signature.
- The sender transmits the digital signature with the message.
- The receiver decrypts the digital signature using the sender's public key, regenerating the sender's message digest.
- The receiver computes a message digest from the message data received and verifies that the two digests are the same.
Figure 1 illustrates this process.
Figure 1. The digital signature process
If the digital signature is verified, the receiver knows that:
- The message has not been modified during transmission.
- The message was sent by the entity that claims to have sent it.
Digital signatures are part of integrity and authentication services. Digital signatures also provide proof of origin. Only the sender knows the private key, which provides strong evidence that the sender is the originator of the message.
We can also encrypt the message itself, which protects the confidentiality of the information in the message.
Parent topic:
Cryptographic concepts