Configure LDAP ACL management (WebSphere Application Server V8.x)
Use LDAP to define the users and groups who can install mobile applications with the Application Center with the Virtual Member Manager (VMM) API. We will define three properties: uid, sn, and cn. These properties enable the login name, and the full name of users and the name of user groups, to be identified in the Application Center. Then we should enable ACL management with VMM. We can configure LDAP based on the federated repository configuration only.
- Log in to the WebSphere Application Server console and go to...
-
Security | Global security | User account repository | Configure | LDAP repository | Additional Properties | LDAP attributes | [WebSphere Application Server V8.0) | WebSphere Application Server V8.5] | Add | Supported
- Enter these property values:
Name LDAP login attribute Property name uid Entity types LDAP entity type - Click OK.
Associating LDAP login with uid property (WebSphere Application Server V8.0)

- Select...
-
Add | Supported
...and set...
Name LDAP attribute for full user name Property name sn Entity types LDAP entity type - Click OK.
Associating LDAP full user name with sn property (WebSphere Application Server V8.0)
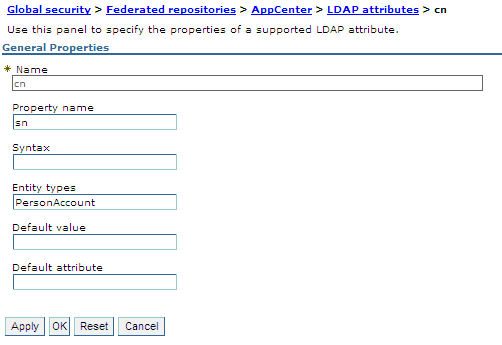
- To configure a group name:
-
Add | Supported
...and set...
Name LDAP attribute for the group name. Property name cn Entity types LDAP entity type - Click OK.
- Enable ACL management with LDAP:
- For each server in cluster, go to...
-
Servers | Server Types | WebSphere application servers | application_server | Configuration Server | Infrastructure | Java and Process Management | Process definition | Configuration tab | Additional Properties | JVM | Configuration | Additional Properties | Custom properties | New
...and set...
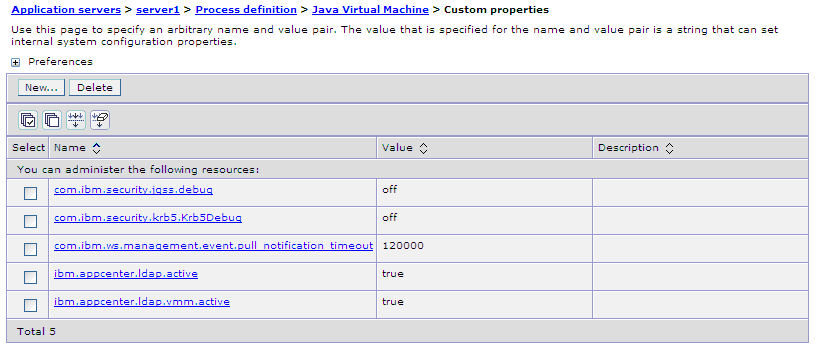
- ibm.appcenter.ldap.vmm.active = true
- ibm.appcenter.ldap.active = true
- ibm.appcenter.ldap.cache.expiration.seconds = delay_in_seconds
Changes to users and groups on the LDAP server become visible to the Application Center after a delay, specified by...
-
ibm.appcenter.ldap.cache.expiration.seconds
Default is 86400 (24 hours)
The Application Center maintains a cache of LDAP data. Changes only become visible after the cache expires. By default, the delay is 24 hours. To clear the cache immediately...
-
acdeploytool.sh \
-clearLdapCache \
-s serverurl \
-c context \
-u user \
-p passwordACL management for Application Center with LDAP on WebSphere Application Server V8
- Save the configuration and restart the server.
- For each server in cluster, go to...
- To use the VMM API, assign the "IdMgrReader" role to the users who run the VMM code, or to the group owners of these users. We must assign this role to all users and groups who have the roles of "appcenteruser" or "appcenteradmin". Run...
-
cd was_home/bin
./wsadmin...and execute...
- $AdminTask mapIdMgrGroupToRole {-roleName IdMgrReader -groupId myLDAP_group_id}
Run the same command for all the groups mapped to the roles of "appcenteruser" and "appcenteradmin".
- For individual users who are not members of groups, run the following command:
- $AdminTask mapIdMgrUserToRole {-roleName IdMgrReader -userId myLDAPid}
- We can assign the special subject "All Authenticated in Application's Realm" as roles for appcenteruser and appcenteradmin. To assign this special subject...
-
$AdminTask mapIdMgrGroupToRole {-roleName IdMgrReader -groupId ALLAUTHENTICATED}
exit
Parent topic: LDAP with WAS v8.x