Implementing basic authenticators
We can implement basic authentication in mobile applications.
The basic authenticator implements basic HTTP authentication. Basic authentication is an industry-standard method used to collect user name and password information.
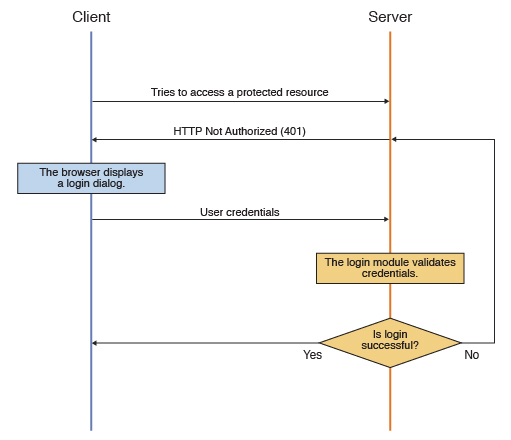
In accordance with standard basic authentication, MobileFirst Server sends an HTTP Not Authorized (401) response to the client, with the header: WWW-Authenticate: Basic realm="realmName". When MobileFirst Server receives the response from the client, it extracts the base64-encoded credentials from the Authorization header of the request and decodes them. A login module validates the credentials that have been received.
We can use basic authentication for web applications only, not for mobile applications.
Fully qualified Java class name for the basic authenticator is:
- com.worklight.core.auth.ext.BasicAuthenticator
- Parameters
-
The basic authenticator has the following parameter:
Parameter Description <basic-realm-name> Mandatory. A string that is sent to the client as a realm name, and presented by the browser in the login dialog.
- Flow
-
The following diagram illustrates the flow in the basic authentication process:
Figure 1. Basic authentication process
- Configure authenticationConfig.xml.
See The authentication configuration file.
- Code the server side.
To protect an adapter procedure with basic authentication, we must declare it in the adapter XML file. See the example in this page.
- Associate the basic authenticator with a login module. MobileFirst Studio provides several predefined login modules. For an example, see Non-validating login module.
- Code the client side, if necessary.
Example
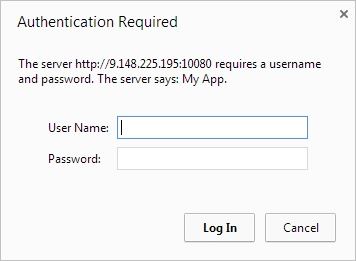
The following example demonstrates how to implement a simple basic authentication mechanism. An adapter procedure is protected by a basic authenticator, and when the user attempts to invoke the procedure from the application, the browser displays a login dialog and the authentication process starts.
Figure 2. Login dialog for authentication
- Configuration of authenticationConfig.xml./dt>
-
<securityTests> <customSecurityTest name="DummyAdapter-securityTest"> <test isInternalUserID="true" realm="MyAppRealm"/> </customSecurityTest> </securityTests> <realms> <realm name="MyAppRealm" loginModule="StrongDummy"> <className>com.worklight.core.auth.ext.BasicAuthenticator</className> <parameter name="basic-realm-name" value="My App"/> </realm> </realms> <loginModules> <loginModule name="StrongDummy"> <className>com.worklight.core.auth.ext.NonValidatingLoginModule </className> </loginModule> </loginModules>The realm uses the StrongDummy login module, which is implemented by the class NonValidatingLoginModule (see Non-validating login module). "Non-validating" means that the user credentials are not checked against any list of user names and passwords. In other words: any combination of user name and password is valid.
- Coding the server side
-
- Create a MobileFirst adapter.
- Add a procedure and protect it with the custom security test created earlier. This procedure's implementation can return some
hard-coded value, for example:
- <procedure name="getSecretData" securityTest="DummyAdapter-securityTest"/>
- Create a MobileFirst adapter.
- Coding the client side
-
- Create a MobileFirst application.
- Write a call to the adapter procedure that we added on the server side, for example:
var invocationData = { adapter: <adapterName>, procedure: "getSecretData", parameters: [] }; WL.Client.invokeProcedure(invocationData, { onSuccess : successCallback, onFailure : failCallback });
- Create a MobileFirst application.
Parent topic: Configure authenticators and realms