Controlling authenticity testing for an app
We can control authenticity testing for apps that connect to the MobileFirst Server.
When an app first connects to the MobileFirst Server, the server tests the authenticity of the app. This test helps to protect apps against some malware and repackaging attacks. This option is available for iPhone, iPad, Android, and Windows Phone 8 apps.
The application developer must configure the app to enable authenticity testing (see MobileFirst security framework for details).
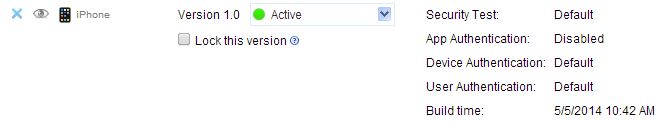
- If the app is configured with authenticity testing disabled for a specific version, then the Authenticity Testing drop down menu in the Console is disabled. An example for the iPhone environment is shown in the following figure.
Figure 1. Authenticity testing disabled for iPhone
- If the app is configured with authenticity testing enabled for a specific version, then the Authenticity Testing drop-down menu in the Console is enabled. An example for the Android environment is shown in the following figure.
Figure 2. Authenticity testing enabled for the Android environment
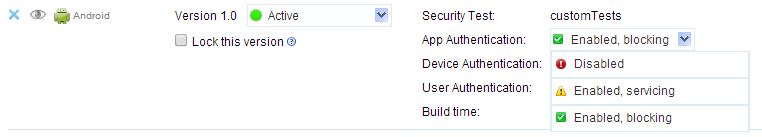
The menu has three options:
- Disabled – the MobileFirst Server does not test the authenticity of the app (despite the developer's settings).
- Enabled, servicing – the MobileFirst Server tests the authenticity of the app. If the app fails the test, the MobileFirst Server outputs
an information message to the log but services the app.
- Enabled, blocking – the MobileFirst Server tests the authenticity of the app. If the app fails the test, the MobileFirst Server outputs an information message to the log and blocks the app.
The authenticity feature is only enabled for apps that use the customer version of the MobileFirst Development Studio. Since the non-customer version of the studio is available on the web, it is a common developer mistake to use it instead of the customer version.
Parent topic: Administer MobileFirst applications with operations console