IBM BPM, V8.0.1, All platforms > Securing IBM BPM and applications > Get started with security
Create end-to-end security
There are a number of potential end-to-end security scenarios, each involving differing security steps. Several typical scenarios, with the necessary security options, are presented in this topic.
These scenarios all assume that administrative security is enforced.
Procedure
- Determine which of the examples provided in this section most closely match your security needs. In some instances, your needs might involve a combination of information from more than one of the scenarios.
- Read the security information for the relevant scenarios and apply it to your security needs.
Example
The following examples illustrate common scenarios.- Example: Classic integration scenario (inbound and outbound adapters)
-
An inbound request comes in from a WebSphere Business Integration Adapter. The Service Component Architecture invokes an interface map based on the SCA export. The request flows through a process component and a second interface map and is then passed on to a second EIS (B), by way of a WebSphere Adapter. These are SCA invocations, with one component invoking a method on the next component.
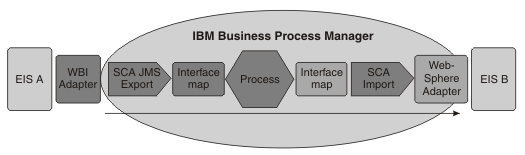
There is no authentication mechanism for the inbound adapter. You can establish the security context by defining the SecurityIdentity qualifier on the first component (in this instance, the first interface map component). From that point, SCA will propagate the security context from each component to the next. Access control for each component is defined by use of the SecurityPermission qualifier.
- Example: Inbound web service request
-
In this scenario, a web service client invokes a component in IBM BPM. The request passes through several components in the IBM BPM environment before being passed to an EIS by an adapter.
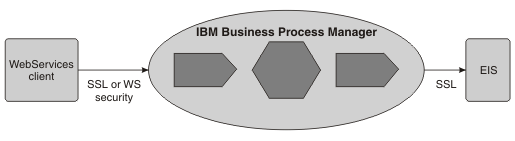
You can authenticate the web service client as an SSL client, using HTTP Basic authentication or using WS-Security authentication. When the client is authenticated, access control is applied based on the SecurityPermission qualifier. Between the client and the IBM BPM instance, you can secure the data integrity and privacy using SSL or WS-Security. SSL secures the entire pipe, whereas with WS-Security, you can encrypt or digitally sign parts of the SOAP message. For web services, WS-Security is the preferred standard.
- Example: Outbound web service request
-
In this scenario, the inbound request can be from an adapter, a web service client, or an HTTP client. A component in IBM BPM (for example a BPEL component) invokes an external web service.

As for the inbound web service request, you can authenticate with the external web service as an SSL client, using HTTP Basic authentication or using WS-Security authentication. Use LTPACallBackHandler as the callback mechanism to extract the usernameToken from the current RunAs subject. Between IBM BPM and the target web service, you can ensure data privacy and integrity using WS-Security.